Imagine you re a malware writer and you need to protect your binary file.
Irp hook removal tool.
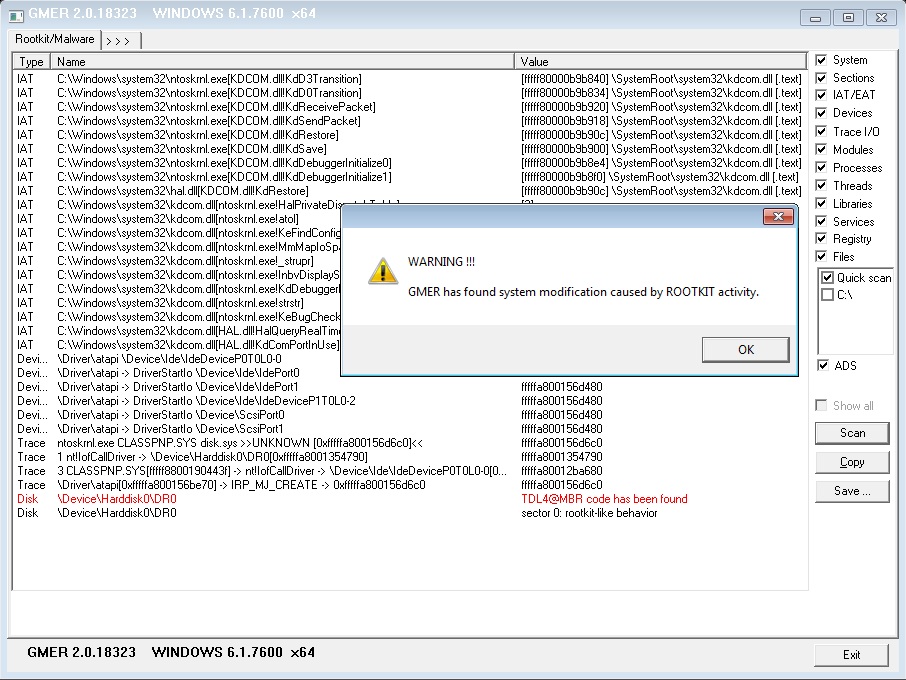
We ran a full computer scan in our avg business edition and see the whole list of irp hook but they are hidden to avg and avg isn t capable of remving them.
Esg security researchers note that removing the irp hook rootkit trojan will often require the use of a specialized anti rootkit tool or an advanced anti malware program with an integrated anti rootkit solution.
If your anti malware software is detecting an irp hook rootkit trojan this may mean that you have a corrupted driver file.
Irp hook rootkit removal free download rootkit hook analyzer bitdefender rootkit remover 64 bit bitdefender rootkit remover 32 bit and many more programs.
Know how you can delete this infectious tricky trojan.
Please help and provide a solution that will get rid of them and hopefully the internet connection and network access will be restored.
Irp hook c windows system32 drivers hidusb sys irp mj close i have searched the web several times and some claim that the threat is fake and others say otherwise.
The remaining viruses are irp hook viruses.
Irp hook practical case.
Irp hook rootkit is able to change browser setting redirects search engine and homepage and it may lead to being stolen sensitive information.
Irp hook rootkit trojan does all malicious activities and remains hidden in the system to evade anti virus scans.
Our free step by step guide works well when the irp hook rootkit virus is in initial stages.
How to remove irp hook rootkit virus steps.
Irp hook rootkit may result in computer getting stuck or hanging when you do some work boot sector getting damage or sometime you finding that your system without response.
4 4 out of 5 stars 145.
If you cannot connect to the internet or.
Deny access to a file.
You don t want anyone to be able to remove your malware so you protect the file.
To remove irp hook rootkit virus try to follow these steps.
When i view details of the threats there are two threats the one that has been solved is part of the operating system while the other that is still.
The threats are called.
5 coupon applied at checkout save 5 with coupon some sizes colors.